
For small and medium businesses (SMBs), the message is clear: you are in the firing line. The report’s early charts show low-level malicious activity is highest among small organisations, a sign that automated phishing, credential theft and commodity malware keep probing the path of least resistance. These incidents are called “low-level,” yet they regularly open the front door to bigger problems like account takeover, data theft and ransomware.
ASD also highlights what hurts businesses most. The top self-reported threats are Email Compromise, Business Email Compromise (BEC) fraud, and Identity Fraud. All three are people-centred and email-driven, which explains why better authentication, email security and staff awareness deliver outsized risk reduction for SMBs.
ASD Cyber Threat Report PDF
The report goes beyond symptoms and explains the root causes. Edge devices and legacy IT expand the attack surface. Information-stealer malware fuels credential reuse and lateral movement. DDoS activity continues to rise, disrupting online services. And generative AI lowers the barrier for criminals to craft convincing lures at scale. In short, threat actors move faster, automate more and reuse stolen data across multiple scams.
Most importantly, ASD tells businesses where to focus. Their four “big moves” are practical and doable for SMBs:
- Implement effective logging so you can see and investigate attacks.
- Replace or isolate legacy IT to remove easy entry points.
- Manage third-party risk so suppliers don’t become your back door.
- Start planning for post-quantum cryptography, so long-lived data remains safe into the 2030s.
In this article we unpack those findings for SMBs, show the page-11 chart where small organisations top the list for low-level attacks, and explain the page-14 business threat breakdown. We then map ASD’s guidance to practical controls in Google Workspace and the Essential Eight, so you can turn national-level insights into everyday protection.
The Data: Small Organisations Are Hit the Hardest
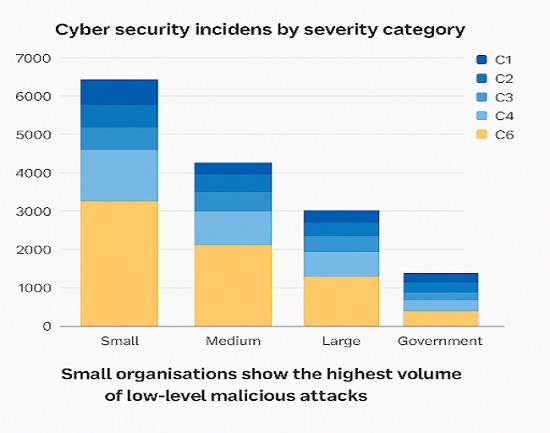
The ASD Cyber Threat Report 2024–2025 does more than tell us who is attacking Australia. It shows where the damage is happening. One of the clearest findings appears on page 11, where ASD charts cyber incidents by severity and organisation size.
That graph reveals a clear pattern. Small organisations are experiencing more low level malicious attacks than any other sector, including large enterprises and government agencies. These incidents fall under Category 6 (C6), considered the least severe on ASD’s scale, yet their frequency makes them impossible to ignore.
These so-called “low level” events usually involve phishing attempts, password theft and opportunistic malware infections. While each attack may appear minor, together they form a constant background risk. If not addressed, this activity can escalate into serious compromises such as ransomware, data breaches or stolen credentials being reused across business systems.
The ASD’s finding reinforces what many already know. Attackers focus on smaller organisations because they often have fewer layers of defence and limited visibility into early warning signs. In short, these small scale attacks are early indicators of much larger risks.
See Figure 1 on page 11 of the for the full breakdown.
Why Small Businesses Are Targeted So Heavily
Cybercriminals go where the defenses are weakest and the rewards are easiest to reach. The ASD Cyber Threat Report shows that small and medium businesses have become a preferred target because they often sit in the middle of the digital supply chain. They handle valuable information, connect to larger organisations, and rely on the same online tools as major enterprises, but without the same level of security oversight. This mix of accessibility, trust and limited protection makes them an attractive focus for attackers who want quick wins with minimal effort.
Key reasons include:
- Lower security maturity: Many SMBs lack dedicated cybersecurity staff or well tested incident response procedures.
- Valuable data with weaker defences: Even small companies hold sensitive client, payroll and financial information that can be easily used for profit.
- Supply chain exposure: Attackers often exploit smaller partners in larger ecosystems to move into bigger targets.
- High success rate through human error: Phishing and social engineering remain the most successful and low cost methods for criminals.
Small organisations often see cybersecurity as an IT expense rather than a business risk, yet the ASD report proves that even low level attacks can accumulate into costly breaches.
Key Cybercrime Trends for Businesses in 2024–2025
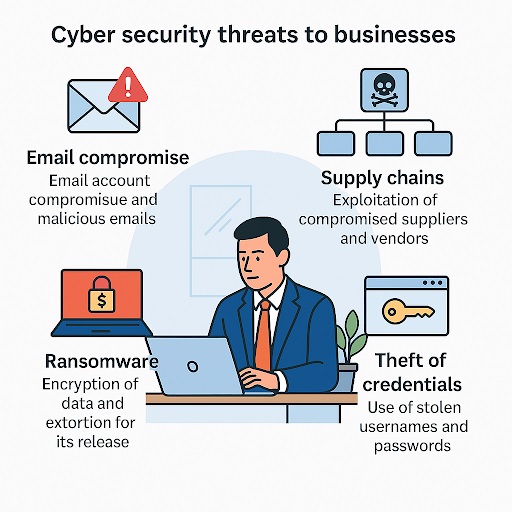
The ASD Cyber Threat Report 2024–2025 provides a detailed look at how Australian businesses are being targeted and where the biggest losses occur. On page 14, the report highlights that the majority of incidents stem from attacks that exploit people rather than technology. Email remains the most common entry point for criminals, with scams and credential theft leading to significant financial and reputational damage. These trends show that while technical defences are essential, the greatest risks now come from everyday business communication and human behaviour. The report identifies three major threats that every organisation should be aware of:
- Email compromise with no financial loss (19%)
- Usually caused by stolen credentials or unauthorised mailbox access.
- Even without immediate loss, these breaches often lead to later fraud or data theft.
- Business Email Compromise (BEC) fraud (15%)
- Direct financial losses through invoice fraud or redirection of payments.
- The average cost of cybercrime for SMBs rose sharply this year:
Small business: $56,600 (↑14%)
Medium business: $97,200 (↑55%)
- Identity fraud (11%)
- Attackers reuse stolen personal or company identities to open credit lines, conduct scams, or impersonate staff in social engineering campaigns
These figures reveal that attackers are increasingly focusing on human-driven vulnerabilities, exploiting trust and communication channels rather than complex technical exploits.
What These Findings Mean for Australian SMBs
The report shows that cybercrime against SMEs is not slowing down in fact, it’s accelerating.
For every large-scale ransomware headline, there are hundreds of unnoticed small-scale incidents: password leaks, phishing clicks, and unauthorised email forwarding rules that quietly compromise entire networks.
Key Takeaways for Business Owners
- No business is “too small” to be a target.
- Attackers use automated tools that scan the internet for any weak link.
- Basic defenses stop most incidents.
- The ASD notes that enabling Multi-Factor Authentication (MFA), patching software, and maintaining strong backups can prevent over 80% of reported incidents.
- Email remains the weakest point.
- Small businesses should deploy email security gateways and phishing simulations to reduce human error.
- Incident response readiness is critical.
- Knowing who to contact and what steps to take can prevent a single breach from escalating into a business-ending event.
Building Resilience: How Sentry Cyber Helps SMBs
The ASD report underscores a clear message: Australian organisations must uplift their cyber maturity now. Sentry Cyber specialises in helping small and medium businesses achieve exactly that.
Our services are designed around the ASD’s recommendations and the Essential Eight maturity model.
Why Does Your Business Need SMB1001?
1. SMBs Are a Prime Target
Cybercriminals increasingly target small businesses because they’re seen as low-hanging fruit—often under-protected and under-prepared. SMB1001 equips your business to withstand threats like phishing, ransomware, and invoice fraud.
2. It’s Built for You
Where other frameworks feel like a square peg in a round hole, SMB1001 is designed specifically for SMBs. It recognises your budget limitations, your lean teams, and your need for simplicity without sacrificing effectiveness.
3. It Builds Trust
Achieving SMB1001 certification shows your clients, suppliers, and partners that you take security seriously. It’s a signal of maturity and accountability—especially when dealing with sensitive data or government contracts.
4. It Helps You Qualify for Cyber Insurance
Many insurers now accept SMB1001 Silver or higher as a benchmark for cybersecurity readiness. With certification in hand, you can unlock better coverage and faster approval.
5. It’s Affordable and Achievable
The first three certification levels—Bronze, Silver, and Gold—are self-attested. That means you don’t need to pay for external audits until you’re ready for higher tiers. You can build your security posture in a structured, cost-effective way.
Why Choose Sentry Cyber?
Sentry Cyber is an authorised partner of SMB1001, which means we’re approved to help businesses like yours audit, certify, and maintain SMB1001 compliance.
As your trusted partner, we provide:
- Guided audits to assess your current cyber posture
- Help with policy creation, documentation, and evidence gathering
- Technical implementation of SMB1001 controls
- Staff training and leadership briefings
- Ongoing support to maintain and renew your certification
Whether you’re going for Bronze or aiming for Diamond, we’ll walk with you every step of the way.
Key Services for SMB Cyber Resilience
- Comprehensive Security Assessment – Identify vulnerabilities across your Google Workspace, endpoints, and cloud tools.
- 24/7 Cyber Security Monitoring – Detect threats early and respond before they cause harm.
- Cyber Awareness Training – Educate staff to recognise phishing and social engineering attempts.
- Phishing Simulations – Test and improve employee responses to real-world threats.
- Compliance & Certification Services – Align with frameworks like NIST CSF, Essential Eight, and SMB1001 to demonstrate good cyber hygiene.
Every one of these steps directly addresses the weaknesses outlined in the ASD report, helping your business stay resilient and compliant.
Connecting the Dots: National Trends and Local Impact
The ASD’s 2024–2025 report highlights a growing collaboration between government, law enforcement, and private industry. However, cybersecurity remains a shared responsibility.
- 42,500+ calls were made to the Cyber Security Hotline this year (up 16%).
- 84,700+ cybercrime reports were received roughly one every 6 minutes.
- Small businesses accounted for the highest proportion of low-level attacks, showing that attackers are prioritising volume and speed.
Even as government agencies enhance national resilience through initiatives like REDSPICE and Operation Aquila, local organisations must still act. Awareness and prevention are the front lines.
Practical Steps for SMBs Right Now
Following ASD’s advice, every business should immediately:
- Enable phishing-resistant MFA (ideally passkeys).
- Use strong and unique passwords, stored securely in a password manager.
- Patch and update all systems, browsers, and cloud apps.
- Back up data securely and test restoration regularly.
- Train employees on phishing awareness and reporting suspicious emails.
- Engage with the ACSC Partnership Program or trusted cyber partners like Sentry Cyber for ongoing monitoring and support.
For more detail, visit cyber.gov.au or report incidents directly via the Australian Cyber Security Hotline (1300 CYBER1).
Conclusion
The ASD Cyber Threat Report 2024–2025 confirms a critical truth, small businesses are Australia’s most targeted group for cyber attacks. Yet with the right controls, awareness, and partnerships, these risks are manageable.
At Sentry Cyber, we help businesses transition from reactive to proactive, building confidence through visibility, protection, and continuous improvement.
Ready to see how your organisation stacks up?
Book a Complementary Cyber Security Workshop to identify your top vulnerabilities and start improving today.
References:
Australian Signals Directorate – Annual Cyber Threat Report 2024–25 (PDF)
