Small and mid-sized businesses across Australia are under pressure to strengthen their security posture without increasing...

Blog
Join our newsletter
GRC Compliance Services & Cyber Risk Management: A Practical Guide for Australian Businesses
Australian organisations face rising regulatory pressure and increasing cyber threats, which makes GRC compliance services a...
Google Workspace Data Protection: A Complete Guide for Modern Businesses
Google Workspace Data Protection is now a core priority for organisations using Gmail, Drive, Docs, and other cloud services, as...
The Backup Myth: Why Google Workspace Vault Isn’t Real SaaS Backup, and What Your Business Actually Needs
Most businesses assume their Google Workspace data is safe because Google offers tools like Vault. However, this assumption...
Cybersecurity for SMEs in Australia: Practical Solutions & Support for Small Businesses
Cybersecurity for SMEs in Australia is no longer optional. With cyberattacks increasing across the country, small businesses...
How to Secure Google Workspace from Phishing: A Complete Beginner’s Guide
Phishing continues to target organisations that rely on Google Workspace, and attackers use smarter, faster, and more...
SaaS Security Services: The Complete 2025 Guide for Australian Businesses
As more organisations move their operations into the cloud, SaaS Security Services have become essential to keeping data safe,...
Cybersecurity Consultancy: What It Is, How It Works & Why SMBs Need It
Small and medium-sized businesses face more cyber threats than ever, and most lack the in-house expertise to defend themselves....
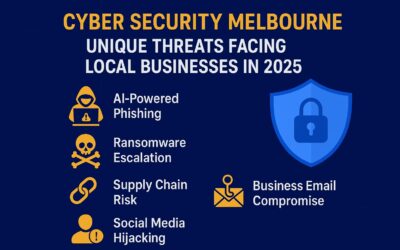
Cyber Security Melbourne: Unique Threats Facing Local Businesses in 2025
Cyber Security Melbourne is becoming a serious priority in 2025, as local businesses face new risks every month. Cybercrime...
Penetration Testing Explained: A Step-by-Step Guide for Beginners
In today’s digital-first world, penetration testing plays a crucial role in defending businesses against cyberattacks. Also...