
Google just announced AI ransomware detection in Google Drive for desktop. It promises to pause sync during an attack and make bulk file recovery simple. That sounds terrific for small and medium businesses. So we ran a controlled ransomware simulation on a test machine with Google Drive for desktop running. We wanted to see if the new protection would spot the encryption behaviour and stop the spread.
In our test, the AI ransomware detection did not trigger. The ransomware encrypted the local files and synced those changes to Drive. We explain what Google’s feature is designed to do, what we observed, and the practical steps every business should take to reduce ransomware risk.
(Official announcement and support docs are linked throughout this article.) Google Workspace
What Google’s AI ransomware detection is designed to do
According to Google, Drive for desktop on Windows and macOS now uses AI to detect patterns consistent with ransomware. When it detects encrypted files during sync, it pauses syncing, raises alerts to the user and admin, and streamlines bulk restoration of clean versions. Google says these capabilities are included in most Workspace commercial plans at no extra cost.
Google’s support documentation adds that ransomware detection is on by default, scans files when they are synced from a desktop to Drive, pauses sync when encryption is suspected, and notifies the user in Drive, via email, and in the Admin console. From there, admins can use the dedicated bulk restore workflow. Google Help
Independent coverage describes the same model: halt syncing, alert quickly, and enable easy file recovery. This is a complement, not a replacement, for antivirus or EDR.
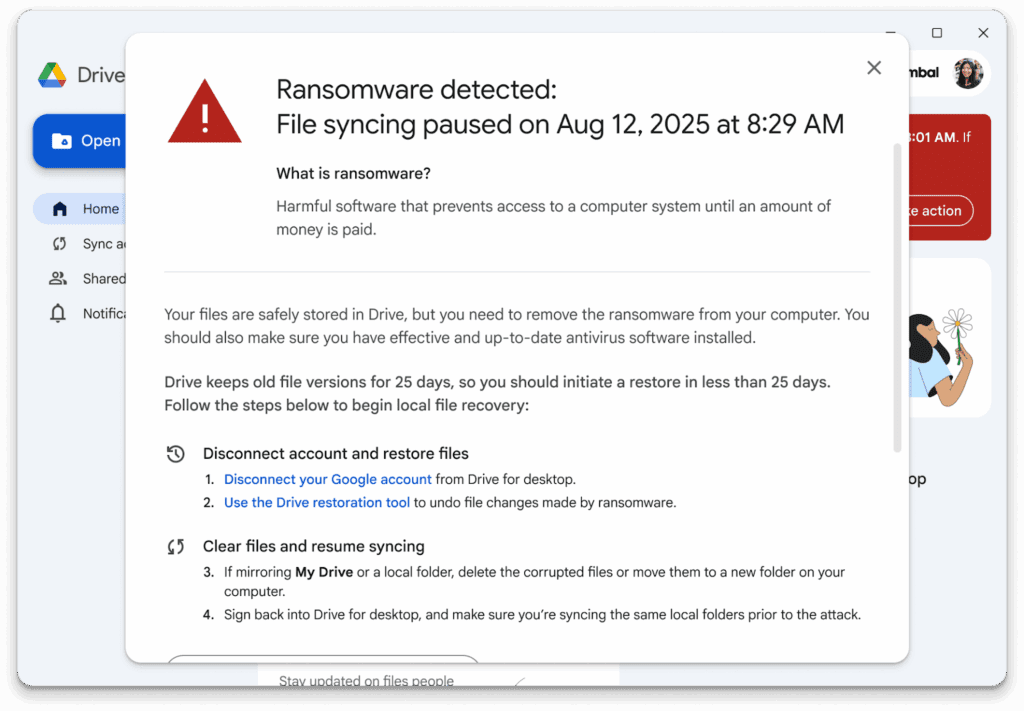
Our controlled simulation: what happened
We executed a known ransomware sample inside a contained virtual machine with Drive for desktop connected and syncing a Documents folder to Google Drive. The aim was to test whether AI ransomware detection in Google Drive would recognise the rapid encryption pattern in time and pause syncing.
Result: in this single test, sync was not paused. The malware encrypted local files, and we observed encrypted versions synchronising to Drive. The suspicious binary also synced to Drive before our endpoint security isolated the host and contained the activity. The embedded video above shows the steps and timing.
This does not prove the feature fails. It simply shows that detection models can miss certain behaviours in the real world. AI-driven defences lower risk, yet they do not remove the need for layered controls like strong EDR, airtight backups, and tight sharing controls. Even Google and industry coverage frame the feature as one layer in defence-in-depth.
How the feature is meant to work (and where gaps can appear)
- Scope: Detection evaluates files during desktop sync. If Drive for desktop is not installed, not running, or if data is outside synced locations, this layer won’t see it. Google Help
- Action on detection: If flagged, Drive pauses sync and alerts the user and admin. Admins can then leverage bulk restore to roll back to a known-good point.
- Limitations: AI reduces spread after compromise. It doesn’t block the initial execution, lateral movement, or credential theft. External reporting also emphasises that it complements existing malware defences rather than replacing them.
What SMBs should do now: a practical, layered plan
1) Keep EDR as your frontline.
Run modern Endpoint Detection and Response on every device. Configure aggressive ransomware rules, isolation, and rollbacks where available. Authoritative guidance stresses a multi-layered program, not one tool.
2) Back up Google Workspace independently.
Use a separate, versioned backup for Gmail, Drive, and Shared Drives with long retention. Backups are the most reliable recovery path when ransomware hits.
→ Sentry can help with Google Workspace backups and security monitoring.
3) Tune Drive for desktop protection and alerts.
Confirm Drive for desktop is deployed where needed, signed-in, and updating. In the Admin console, verify ransomware alerts and the bulk restore process in a test scenario so your team knows the flow.
4) Reduce risky sharing and data sprawl.
Apply least-privilege sharing policies, avoid public links, and watch for unusual sharing spikes. Industry guidance maps these basics to core performance goals.
→ Our Security Assessment and Security Consulting include Drive governance checks.
5) Train staff and simulate attacks.
Most ransomware starts with phishing. Run cyber awareness training and regular phishing simulations so people spot lures fast.
6) Prepare an incident playbook.
Document who to call, how to isolate a machine, how to restore data, and how to notify stakeholders.
7) Mind your SaaS dependencies.
Ransomware increasingly targets identity and SaaS. Harden Google Workspace with DLP, context-aware access, and role hygiene.
→ Explore our NIST Cybersecurity Framework and Essential Eight programs for a structured rollout.
Step-by-step: how to verify Google’s protection
- Check version and deployment: Ensure users run the latest Drive for desktop and that target folders are in scope.
- Confirm alerts: In the Admin console, verify that ransomware alerts are enabled and routed to your security mailbox or SIEM.
- Practice bulk restore: Use Google’s bulk restore workflow on a test dataset to rehearse the steps and timings.
- Run a tabletop exercise: Pair the Drive workflow with your EDR isolate action, comms plan, and service desk script.
Conclusion
Google’s AI ransomware detection in Google Drive is a welcome layer. It can pause sync and speed up recovery when it recognises mass encryption in time. In our simulation, the model did not trigger, which reinforces a simple truth. Ransomware defence must stay layered and well-rehearsed. If you want help verifying Drive for desktop protection, hardening Google Workspace, or standing up independent backups and EDR, book our complimentary workshop and we will map quick wins for your environment.
→ Complimentary cyber security workshop
Frequently asked questions
Q1: Does AI ransomware detection in Google Drive replace antivirus or EDR?
A1: No. Google positions it as an additional layer that detects patterns during sync and helps you restore. You still need full EDR.
Q2: Is the feature on by default?
A2: Yes, for supported Workspace editions. It scans files as they sync from desktop to Drive and pauses on detection.
Q3: Can it protect files outside my Drive sync folders?
A3: No. It only evaluates files within Drive for desktop’s sync scope.
Q4: What’s the safest way to recover after ransomware?
A4: Restore from unaffected backups with strong retention. That advice appears in national guidance for a reason.
Q5. Can I read the official announcement?
A5: See Google’s product blog and support article for details and admin steps. Google Workspace+1
For more FAQ’s click here
